- Lab 1 Differential Power Analysis Total 100 Pts In This Lab We Will Implement The Dpa On Aes Encryption Using The Pow 1 (47.42 KiB) Viewed 50 times
- Lab 1 Differential Power Analysis Total 100 Pts In This Lab We Will Implement The Dpa On Aes Encryption Using The Pow 2 (40.01 KiB) Viewed 50 times
Refrence:
https://drive.google.com/drive/folders/ ... sp=sharing
Lab 1 Differential Power Analysis [Total 100 pts] In this lab, we will implement the DPA on AES encryption using the power trace available in power_trace1.mat. In case you don't have a Matlab installed on your machine, you will need to install Matlab wwwwwww
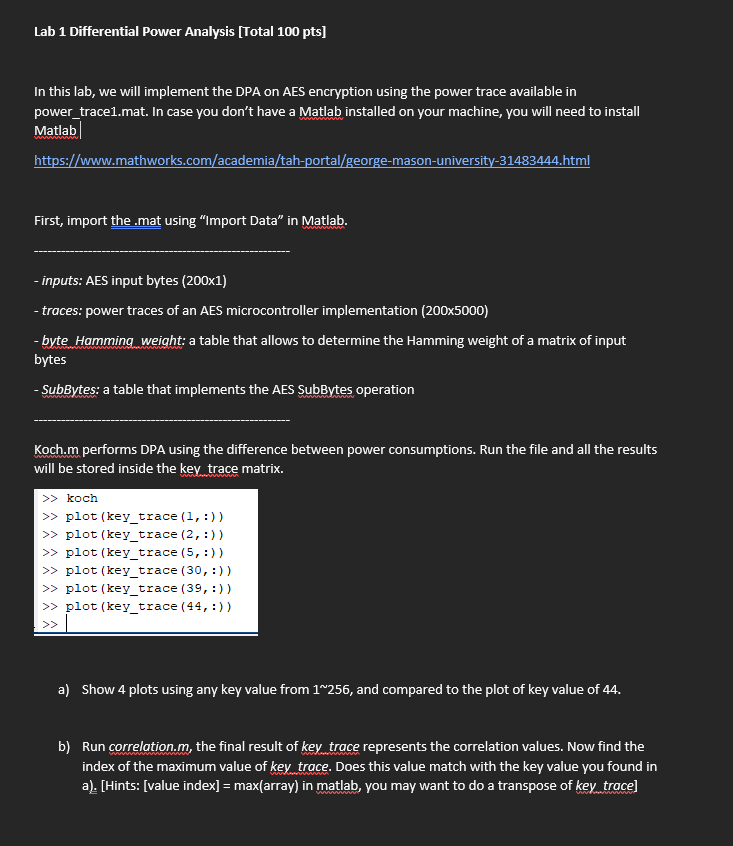
https://www.mathworks.com/academia/tah- ... 83444.html First, import the .mat using "Import Data" in Matlab. - inputs: AES input bytes (200x1) - traces: power traces of an AES microcontroller implementation (200x5000) -byte Hamming weight: a table that allows to determine the Hamming weight of a matrix of input bytes - SubBytes: a table that implements the AES SubBytes operation Koch.m performs DPA using the difference between power consumptions. Run the file and all the results will be stored inside the key trace matrix. >> koch >> plot (key_trace (1,

) >> plot (key_trace (2,

) >> plot (key_trace (5,

) >> plot (key_trace (30,

) >> plot (key_trace (39,

) >> plot (key_trace (44,

) >> a) Show 4 plots using any key value from 1~256, and compared to the plot of key value of 44. b) Run correlation.m, the final result of key trace represents the correlation values. Now find the index of the maximum value of key trace. Does this value match with the key value you found in a). [Hints: [value index] = max(array) in matlab, you may want to do a transpose of key trace]
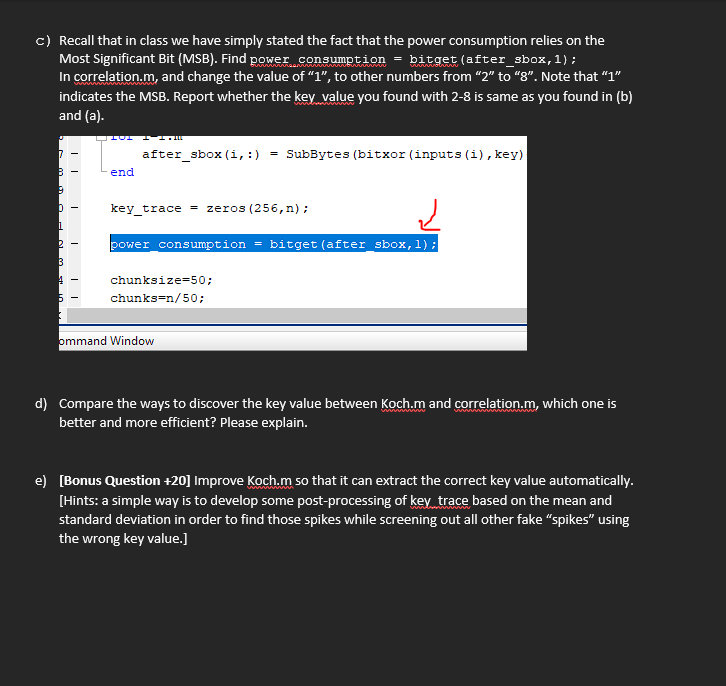
c) Recall that in class we have simply stated the fact that the power consumption relies on the Most Significant Bit (MSB). Find power consumption = bitget (after_sbox, 1); In correlation.m, and change the value of "1", to other numbers from "2" to "8". Note that "1" indicates the MSB. Report whether the key value you found with 2-8 is same as you found in (b) and (a). 7 B 9 b 1 2 3 4 6 end after_sbox (i,

= SubBytes (bitxor (inputs (i), key) 2 power consumption = bitget (after_sbox, 1); key_trace = zeros (256, n) ; chunksize=50; chunks-n/50; ommand Window d) Compare the ways to discover the key value between Koch.m and correlation.m, which one is better and more efficient? Please explain. e) [Bonus Question +20] Improve Koch.m so that it can extract the correct key value automatically. [Hints: a simple way is to develop some post-processing of key trace based on the mean and standard deviation in order to find those spikes while screening out all other fake "spikes" using the wrong key value.]